Osi Model and Cyber Kill Chain
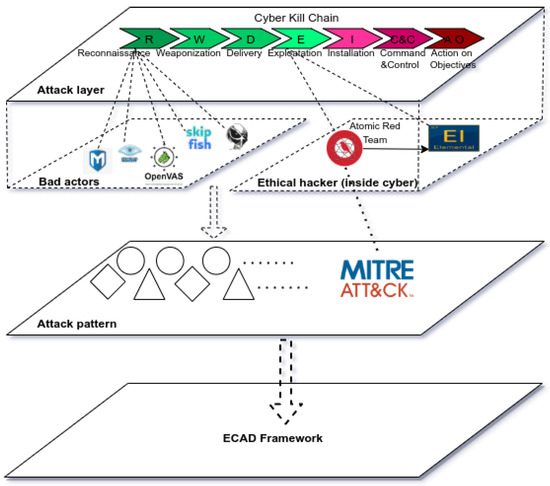
Incident Management and Response The Lockheed Martin Cyber Kill Chain method is the core of our Intelligence Driven Defenseour differentiator in the battle against advanced persistent threats. In this blog we have discussed some of these including the MITRE ATTCK model Yara rules and more recently the Adversarial ML Threat Matrix.
At the end well learn more about Open-Source Tool focused on Malware Hunting to build our Lab.

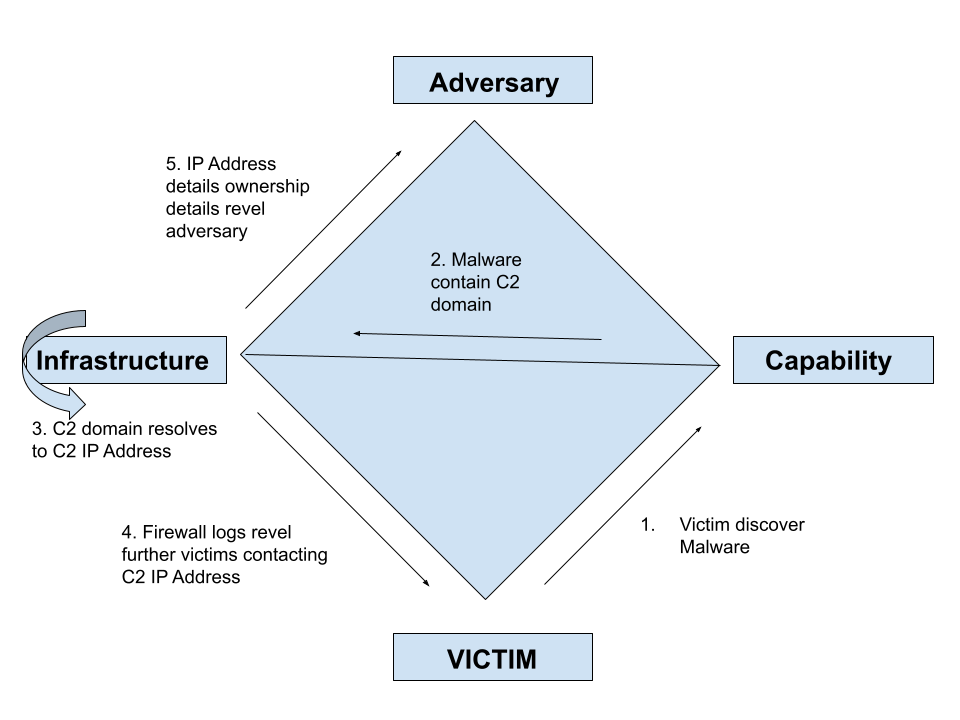
. It specifies common TCPIP protocols used to fight against cyberattacks. Cyber Kill Chain and the Diamond Model Threat Intelligence frameworks have several advantages. The idea behind it is to identify itemise and prevent hostile cyber activity such as intrusion of a network.
Yet the Cyber Kill Chain CKC is also an important and highly useful framework. Understanding Cyber Attacks CKC phases_ The term Kill Chain has military origins. The model identifies what the cyber adversaries must complete in order to achieve their objectives.
They can aid in understanding the attacker as well as help mitigate or eliminate any threats. Developed by Lockheed Martin the Cyber Kill Chain CKC framework is part of the Intelligence Driven Defense model for the identification and prevention of cyber intrusions activity. Step 1 Reconnaissance.
Most cyber attacks follow this general flow. Eisenhower was an Army general and World War II Allied Forces Supreme Commander Prioritize Your Response -1 - Urgency URGENT IMPORTANT - Do It Now SEVERE Imminent Threat Significant Harm. Execution Steps Exploitation Steps Command Control Steps and Lateral Movement Steps.
This article provides a brief insight of. It is a set of metrics designed to create a way to describe security incidents in a structured and repeatable way. Cyber Kill Chain 3 Troubleshooting Process Adversaries OSI Prioritize Your Response Eisenhower Priority Matrix.
Build infrastructure and tools. A better model is Lockheed Martins Cyber Kill Chain. Experienced analysts monitor activities of cyberattackers during an event record the information and use it to defend against them.
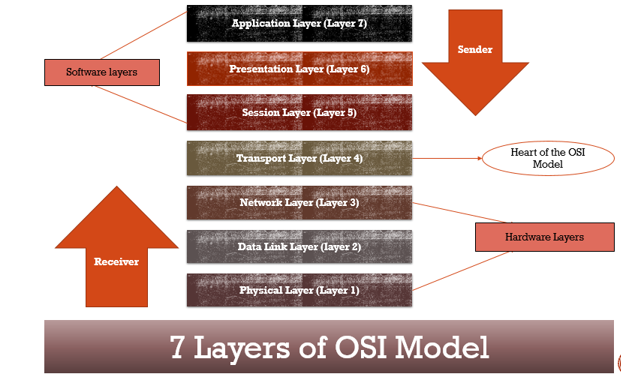
Well describe OSI layers top down from the application layer that directly serves the end user down to the physical layer. The kill chain is a military concept that goes back decades and refers to a defenders ability to disrupt an attack at all of its various stages. The model identifies what the adversaries must complete in order to achieve their objective.
While the above cyber terrain visualization is great for learning the layers of the cyber terrain its a bit busy for cyber-attack analysis visualization. The Cyber Kill Chain is a model that describes and explains various stages of a cyber attack. This article provides a brief insight of.
OSI Model Explained. The application layer is used by end-user software such as web browsers and email clients. The OSI Protocol Model has been around for 30 years and is widely known in the IT industry.
Reconnaissance Weaponization Delivery Exploitation Installation Command and Control. Slide 2 The cyber kill chain is a sequence of stages required for an attacker to successfully infiltrate a network and exfiltrate data from it. The cyber kill chain CKC is a classic cybersecurity model developed by the computer security incident response team CSIRT at Lockheed Martin.
The cyber kill chain developed by Lockheed Martin is an industry-accepted methodology for understanding how an attacker will conduct the activities necessary to cause harm to your organization. For example this is the ransomware kill chain. The purpose of the model is to better understand the stages required to execute an attack and to help security teams stop an attack at each of its stages.
They can aid in understanding the attacker as well as help mitigate or eliminate any threats. It provides protocols that allow software to send and receive. How the Cyber Kill Chain Works in 7 Steps Each stage of the Cyber Kill Chain is related to a certain type of threat both external and internal.
It uses the OSI model to describe cyberattacks at each of the seven layers. The stages of the Kill chain are reconnaissance Weaponization delivery exploit installation command and control and actions. Developed by Lockheed Martin the Cyber Kill Chain framework is part of the Intelligence Driven Defense model for identification and prevention of cyber intrusions activity.
Originally published in 2011 the Cyber Kill Chain shown below outlines seven steps that an attacker takes during an intrusion. RECON STAGE LAUNCH EXPLOIT INSTALL CALL BACK PERSIST Learn about target. Before becoming President Dwight D.
Some critics believe that the methodology also reinforces traditional perimeter-based and. For the most part whatever threat you face from malware phishing insider threats and more it is likely that they will fall into one or more of the activities on the kill chain. One of the biggest critiques of Lockheeds cyber kill chain model is the fact that the first phases reconnaissance weaponization of an attack occur outside the target network which makes it difficult to understand or defend against actions occurring in these phases.
Cyber Kill Chain and the Diamond Model Threat Intelligence frameworks have several advantages. The Cisco cybersecurity portfolio acts across the entire kill chain. Developing Cyber Kill Chain Strategy Part 2 In this module we will continue to learn how to develop the Cyber Kill Chain strategies such as.
It was developed by Lockheed Martin. The Cisco Security portfolio is also simple open and automated to make you more effective. What is the cyber kill chain.
The model identifies what adversaries must complete in order to achieve their objective. This time-honored model has been around the longest and cybersecurity pros and software applications refer to it often. The OSI 7 Layers.

Cyber Kill Chain Applied To Ics Incibe Cert
Cyber Hygiene Attack Analysis Methodology Ciso Central
Cyber Kill Chain Mitre Att Ck Framework Cybermeteoroid

Cyber Kill Chain Applied To Ics Incibe Cert
Cyber Kill Chain Mitre Att Ck Framework Cybermeteoroid

Cyber Kill Chain Explained Steps And Drawbacks

Cyber Kill Chain Applied To Ics Incibe Cert
Osi Model Is Well Explained In Simple Definition With Examples

Ekoda Amandita F Maintenance Staff Pt Lasallefood Indonesia Linkedin

Cyber Kill Chain And Defense Strategy The Security Buddy

Protecting The Organization Cybersecurity Free Online Quiz

The Osi Model And Cyber Attack Examples Originally Published In Download Scientific Diagram

Cyber Security Kill Chain Active Reconnaissance Overview Methodology And Tools Youtube

Cyber Kill Chain Applied To Ics Incibe Cert

The Osi Model And Cyber Attack Examples Originally Published In Download Scientific Diagram

250 It Related Reference Ideas Computer Programming Computer Knowledge Computer Science
Cyber Hygiene Attack Analysis Methodology Ciso Central
Electronics Free Full Text Experimental Cyber Attack Detection Framework Html


Comments
Post a Comment